
Subscribe to my newsletter, The Wavelength, if you want the content on my blog delivered to your inbox four times a week before it’s posted here. The Wavelength will transition to a subscription product early in 2022. Details to come.
Other Developments
- The United Kingdom’s (UK) Secretary of State for Digital, Culture, Media and Sport Oliver Dowden announced that the government has selected New Zealand’s Privacy Commissioner John Edwards to be the next Information Commissioner. Dowden explained:
- Mr Edwards will now appear before MPs on the Digital, Culture, Media and Sport Select Committee for pre-appointment scrutiny on 9th September 2021.
- Under the Data Protection Act, the Information Commissioner is appointed by Her Majesty by Letters Patent on the basis of fair and open competition and on the recommendation from ministers (the Secretary of State for Digital Culture, Media and Sport, through the Prime Minister).
- Ministers were assisted in their decision-making by an Advisory Assessment Panel which included a departmental official and a senior independent panel member approved by the Commissioner for Public Appointments.
- During its markup of its portion of the $3.5 trillion budget reconciliation package, the House Oversight and Reform Committee added $3 billion for United States (U.S.) cybersecurity and information and communications technology (ICT) modernization. The committee adopted an Amendment In The Nature Of A Substitute, and Government Operations Subcommittee Chair Gerry Connolly (D-VA) offered an amendment successfully that adds to the bill the following:
- $1 billion for the Technology Modernization Fund, which would follow the $1 billion appropriated for program in the “American Rescue Plan Act of 2021.”
- $ 2 billion for the General Services Administration’s Federal Citizen Services Fund (FCSF), a program that received $150 million in this year’s COVID stimulus package. In its FY 2022 budget request, the agency explained:
- [The FCSF] enables public access and engagement with the Government through an array of public and agency facing products and programs. The FCSF initiatives help individuals, businesses, other governments, and the media to easily interact with Federal information, services, benefits, and business opportunities. The FCSF supports agency facing programs that drive Government-wide transformation through shared services, platforms, and solutions. The programs funded by the FCSF also provide technical expertise to agencies to improve their operations and the public’s experience with Government in support of the Administration’s priorities and Cross-Agency Priority Goals. The FCSF supports extensive communities of practice to drive adoption and improvement of digital services while also helping agencies develop and share best practices. GSA will continue to leverage the FCSF to support initiatives that drive innovation in Government operations and improve the transparency, efficiency, and effectiveness of Federal operations and quality of Government services.
- In a press release, the committee highlighted electric vehicle funding and asserted their provisions would:
- Provide critical funding to electrify the General Services Administration and United States Postal Service vehicle fleets by providing $12 billion to:
- Position the federal government as a leader in modernizing vehicles to reduce carbon output;
- Build charging stations and support infrastructure across the country; and
- Take a major step towards a fully electric future for federal vehicles.
- Provide critical funding to electrify the General Services Administration and United States Postal Service vehicle fleets by providing $12 billion to:
- The White House’s Office of Management and Budget (OMB) issued a memorandum per a direction in Executive Order 14028 “Improving the Nation’s Cybersecurity” and the agency explained:
- Recent events, including the SolarWinds incident, underscore the importance of increased government visibility before, during, and after a cybersecurity incident. Information from logs on Federal information systems (for both on-premises systems and connections hosted by third parties, such as cloud services providers (CSPs)) is invaluable in the detection, investigation, and remediation of cyber threats.
- Executive Order 14028, Improving the Nation’s Cybersecurity, directs decisive action to improve the Federal Government’s investigative and remediation capabilities. This memorandum was developed in accordance with and addresses the requirements in section 8 of the Executive Order for logging, log retention, and log management, with a focus on ensuring centralized access and visibility for the highest-level enterprise security operations center (SOC) of each agency. In addition, this memorandum establishes requirements for agencies to increase the sharing of such information, as needed and appropriate, to accelerate incident response efforts and to enable more effective defense of Federal information and executive branch departments and agencies.
- Agencies must immediately begin efforts to increase performance in accordance with the requirements of this memorandum. Specifically, agencies must:
- Within 60 calendar days of the date of this memorandum, assess their maturity against the maturity model in this memorandum and identify resourcing and implementation gaps associated with completing each of the requirements listed below. Agencies will provide their plans and estimates to their OMB Resource Management Office (RMO) and Office of the Federal Chief Information Officer (OFCIO) desk officer.
- Within one year of the date of this memorandum, reach EL1 maturity.
- Within 18 months of the date of this memorandum, achieve EL2 maturity.
- Within two years of the date of this memorandum, achieve EL3 maturity.
- Provide, upon request and to the extent consistent with applicable law, relevant logs to the Cybersecurity and Infrastructure Security Agency (CISA) and Federal Bureau of Investigation (FBI). This sharing of information is critical to defend Federal information systems.
- Share log information, as needed and appropriate, with other Federal agencies to address cybersecurity risks or incidents.
- The following agencies bear specialized responsibilities as part of government-wide efforts to improve the management and use of logging practices:
- CISA is responsible for the following actions:
- Deploying teams to advise agencies in their assessment of logging capabilities.
- Developing and publishing tools, in coordination with the FBI, to help agencies facilitate their assessment of logging maturity across the organization.
- The Department of Commerce is responsible for the following actions:
- Continuing to maintain National Institute of Standards and Technology (NIST) Special Publication (SP) 800-92,4 Guide to Computer Security Log Management, in coordination with CISA and the FBI.
- Incorporating the requirements of this memorandum regarding logging, log retention, and log management in the next revision of SP 800-92 and other relevant publications.
- none of your business (noyb) filed 422 complaints with ten European data protection agencies alleging widespread violations of the General Data Protection Regulation (GDPR) regarding cookies. noyb explained:
- As part of a one-year project on “deceptive designs” and “dark patterns”, noyb aims to scan, warn and enforce the GDPR on up to 10.000 websites in Europe. After sending a written warning and a “draft complaint” to more than 500 companies on May 31st, 42% of all violations were remedied within 30 days. However, 82% of all companies have not fully stopped violating the GDPR. Accordingly, noyb filed 422 complaints with ten data protection authorities today.
- 42% of all violations in first batch of 516 websites fixed. In the first batch of complaints, companies remedied 42% of the violations that noyb identified in Spring 2021. Of the companies that previously violated the law in this respect, 42% added a “reject” option. 68% removed “pre-ticked” boxes. 46% solved issues around using different colors for “accept” and “reject” buttons. 22% gave up on claiming that they have a “legitimate interest” that would allow tracking without user consent. Overall, 1028 individual violations across more than 516 websites were removed by the companies. Among the companies that fully stopped using “dark patterns” to gain user consent, are global brands like Mastercard, Procter & Gamble, Forever 21, Seat or Nikon.
- The United Kingdom’s Department for Digital, Culture, Media & Sport (DCMS) announced a “a £5 billion plan to level up internet access across the UK.” The DCMS stated:
- The government’s Project Gigabit fund to upgrade digital infrastructure in hard-to-reach areas will accelerate the country’s recovery from covid, fire up high-growth sectors such as tech and the creative industries, put an end to families battling for bandwidth and bring the speed and reliability people need to start and run businesses.
- New details published today reveal up to 1,850,000 additional premises across 26 English counties will get access to gigabit speed internet of 1,000 megabits per second – enough to download a HD movie in less than 30 seconds and lay the foundations for next-generation tech such as 8K-quality video streaming.
- It brings the current total number of premises in scope for government-funded coverage to 2.2 million, with more still to be announced over the coming months across England, Scotland, Wales and Northern Ireland.
- This is in addition to the tens of millions of premises that broadband firms are rapidly connecting through their commercial rollout, from one in ten households in 2019 to more than two in five today. The UK is also on track for the fastest rollout in Europe this year and for 60 per cent of all households to have access to gigabit speeds by the end of this year.
- The government is also on track to hit its target of achieving at least 85 per cent gigabit-capable UK coverage by 2025, and ministers are ready to go as fast as broadband companies can manage.
- The United States Government Accountability Office (GAO) issued a report titled “Facial Recognition Technology: Current and Planned Uses by Federal Agencies” as requested by the chair and ranking member of the House Oversight and Reform Committee and the ranking member of the House Judiciary Committee. The GAO found:
- In response to GAO’s survey about facial recognition technology (FRT) activities in fiscal year 2020, 18 of the 24 surveyed agencies reported using an FRT system, for one or more purposes, including:
- Digital access or cybersecurity. Sixteen agencies reported using FRT for digital access or cybersecurity purposes. Of these, 14 agencies authorized personnel to use FRT to unlock their agency-issued smartphones—the most common purpose of FRT reported. Two agencies also reported testing FRT to verify identities of persons accessing government websites.
- Domestic law enforcement. Six agencies reported using FRT to generate leads in criminal investigations, such as identifying a person of interest, by comparing their image against mugshots. In some cases, agencies identify crime victims, such as exploited children, by using commercial systems that compare against publicly available images, such as from social media.
- Physical security. Five agencies reported using FRT to monitor or surveil locations to determine if an individual is present, such as someone on a watchlist, or to control access to a building or facility. For example, an agency used it to monitor live video for persons on watchlists and to alert security personnel to these persons without needing to memorize them.
- Ten agencies reported FRT-related research and development. For example, agencies reported researching FRT’s ability to identify individuals wearing masks during the COVID-19 pandemic and to detect image manipulation.
- Furthermore, ten agencies reported plans to expand their use of FRT through fiscal year 2023. For example, an agency plans to pilot the use of FRT to automate the identity verification process at airports for travelers.
- The GAO provided these examples of federal FRT use:
- In response to GAO’s survey about facial recognition technology (FRT) activities in fiscal year 2020, 18 of the 24 surveyed agencies reported using an FRT system, for one or more purposes, including:
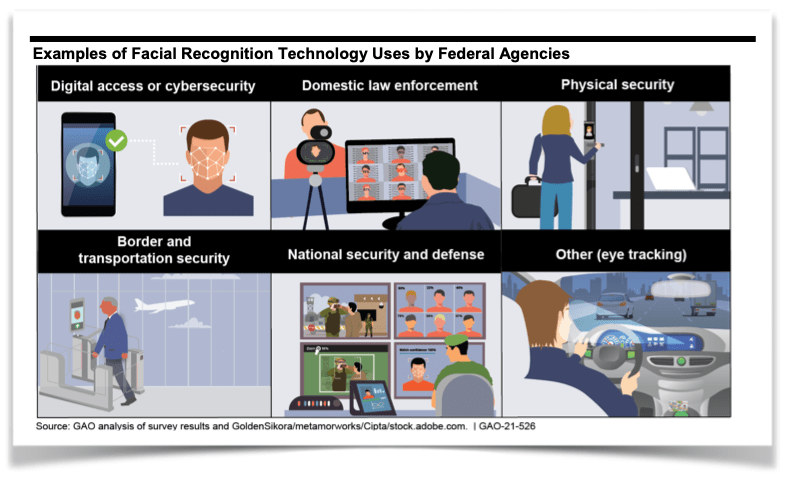
- The GAO variously noted:
- Most of the federal agencies we surveyed—19 of 24—reported one or more FRT-related activities in fiscal year 2020, with digital access and domestic law enforcement as the most common.

- New Zealand’s Financial Markets Authority (FMA) issued “an information sheet containing principles and resources to help licensed financial advice providers develop their cyber resilience.” The agency added:
- Financial advice provider licensing was introduced in March 2021 as part of the new regime for regulating financial advice under the Financial Markets Conduct Act 2013 (as amended by the Financial Services Legislation Amendment Act 2019).
- The standard conditions for full financial advice providers licences include a requirement to have and maintain a business continuity plan that includes procedures for responding to, and recovering from, events that impact on cybersecurity and continuity (condition 5).
- Additionally, the new Code of Professional Conduct for Financial Advice Services requires providers to ensure that client information is protected against loss and unauthorised access, use, modification or disclosure.
- The World Health Organization (WHO) issued “a guidance document for countries and implementing partners on the technical requirements for developing digital information systems for issuing standards-based interoperable digital certificates for COVID-19 vaccination status, and considerations for implementation of such systems, for the purposes of continuity of care, and proof of vaccination.” The WHO stated:
- In the context of the coronavirus disease (COVID-19) pandemic, the concept of Digital Documentation of COVID-19 Certificates (DDCC) is proposed as a mechanism by which a person’s COVID-19-related health data can be digitally documented via an electronic certificate. A digital vaccination certificate that documents a person’s current vaccination status to protect against COVID-19 can then be used for continuity of care or as proof of vaccination for purposes other than health care. The resulting artefact of this approach is referred to as the Digital Documentation of COVID-19 Certificates: Vaccination Status (DDCC:VS).
- The current document is written for the ongoing global COVID-19 pandemic; thus, the approach is architected to respond to the evolving science and to the immediate needs of countries in this rapidly changing context; for this reason, the document is issued as interim guidance. The approach could eventually be extended to capture vaccination status to protect against other diseases.
- The document is part of a series of guidance documents (see Fig. 1) on digital documentation of COVID-19-related data of interest: vaccination status (this document), laboratory test results, and history of SARS-CoV-2 infection.
- The World Health Organization (WHO) has developed this guidance and accompanying technical specifications, in collaboration with a multidisciplinary group of partners and experts, in order to support WHO Member States in adopting interoperable standards for recording vaccination status. The audience of this document is therefore Member States and their implementing partners that want to put in place digitally signed vaccination records.
- The Federal Communications Commission’s (FCC) Wireline Competition Bureau announced the “final procedures for, and provides eligible providers of advanced communications services with additional guidance regarding, the application filing and reimbursement process for the $1.9 billion Secure and Trusted Communications Networks Reimbursement Program (Reimbursement Program).” The FCC explained:
- The Secure and Trusted Communications Networks Act of 2019 (Secure Networks Act) directs the Commission to establish the Reimbursement Program. The Reimbursement Program will reimburse providers of advanced communications services with ten million or fewer customers for costs incurred in the removal, replacement, and disposal of covered communications equipment or services that pose a national security risk, i.e., communications equipment or services produced or provided by Huawei Technologies Company (Huawei) or ZTE Corporation (ZTE), that were obtained by providers on or before June 30, 2020.
- On July 13, 2021, the Commission adopted the 2021 Supply Chain Order, which amended the Commission’s rules to incorporate the Consolidated Appropriations Act, 2021 (CAA) amendments to the Secure Networks Act. Specifically, the 2021 Supply Chain Order (1) increased the customer eligibility cap for participation in the Reimbursement Program from 2 million or fewer customers to 10 million or fewer customers; (2) modified the type of equipment and services eligible for reimbursement to be limited to communications equipment and services produced or provided by Huawei or ZTE that are on the Covered List; (3) adjusted the date by which equipment or services must have been obtained to be eligible for Reimbursement Program funds to June 30, 2020; (4) adopted the prioritization scheme created in the CAA; (5) clarified the definition of “provider of advanced communications service” for the purposes of the Reimbursement Program; and (6) clarified portions of the Reimbursement Program to assist eligible providers seeking reimbursement.
- The United States (U.S.) Department of Homeland Security published a final rule on “Cybersecurity Talent Management System” and stated:
- The U.S. Department of Homeland Security (DHS) is establishing a new talent management system to address DHS’s historical and ongoing challenges recruiting and retaining individuals with skills necessary to execute DHS’s dynamic cybersecurity mission. The Cybersecurity Talent Management System (CTMS) is a mission-driven, person-focused, and market-sensitive approach to talent management. CTMS represents a shift from traditional practices used to hire, compensate, and develop Federal civil service employees and is designed to adapt to changes in cybersecurity work, the cybersecurity talent market, and the Department’s cybersecurity mission. CTMS will modernize and enhance DHS’s capacity to recruit and retain mission-critical cybersecurity talent. With CTMS, DHS is creating a new type of Federal civil service position, called a qualified position, and the cadre of those positions and the individuals appointed to them is called the DHS Cybersecurity Service (DHS-CS). CTMS will govern talent management for the DHS-CS through specialized practices for hiring, compensation, and development. Individuals selected to join the DHS-CS will be provided with a contemporary public service career experience, which emphasizes continual learning and contributions to DHS cybersecurity mission execution. This rulemaking adds regulations to implement and govern CTMS and the DHS-CS.
- An Illinois court rejected Clearview AI’s motion to dismiss and now the American Civil Liberties Union (ACLU) may proceed with its suit under the Illinois Biometric Information and Privacy Act (BIPA), 740 ILCS 14/1et seq.
- The court provided the background:

- The court summarized the ACLU’s claims:

- The court summarized Clearview AI’s arguments:

Further Reading
- “La Puente man steals 620,000 iCloud photos in plot to find images of nude women” By Michael Finnegan — The Los Angeles Times. A Los Angeles County man broke into thousands of Apple iCloud accounts and collected more than 620,000 private photos and videos in a plot to steal and share images of nude young women, federal authorities say. Hao Kuo Chi, 40, of La Puente, has agreed to plead guilty to four felonies, including conspiracy to gain unauthorized access to a computer, court records show.
- “A Bad Solar Storm Could Cause an ‘Internet Apocalypse’” By Lily Hay Newman — WIRED. Scientists have known for decades that an extreme solar storm, or coronal mass ejection, could damage electrical grids and potentially cause prolonged blackouts. The repercussions would be felt everywhere from global supply chains and transportation to internet and GPS access. Less examined until now, though, is the impact such a solar emission could have on internet infrastructure specifically. New research shows that the failures could be catastrophic, particularly for the undersea cables that underpin the global internet.
- “T-Mobile Hacker Who Stole Data on 50 Million Customers: ‘Their Security Is Awful’” By Drew FitzGerald and Robert McMillan — The Wall Street Journal. The hacker who is taking responsibility for breaking into T-Mobile US Inc.’s systems said the wireless company’s lax security eased his path into a cache of records with personal details on more than 50 million people and counting. John Binns, a 21-year-old American who moved to Turkey a few years ago, told The Wall Street Journal he was behind the security breach. Mr. Binns, who since 2017 has used several online aliases, communicated with the Journal in Telegram messages from an account that discussed details of the hack before they were widely known.
- “China squeezes kids’ online gaming time to 3 hours a week” By Carrie Mihalcik — c/net. China is tightening its restrictions on online gaming for kids and teens. Chinese officials on Monday issued rules that will limit the time minors are allowed to play online games to just one hour a day on weekends and holidays, according to state-run news agency Xinhua. The new rules, released by the National Press and Publication Administration, are focused on “anti-addiction” measures and reportedly follow complaints from parents that the previous restrictions were too generous. Under rules put in place in 2019, minors were limited to one and a half hours of online gaming on weekdays and three hours on weekends.
- “Cyber insurance market encounters ‘crisis moment’ as ransomware costs pile up” By Tim Starks — cyberscoop. It’s a sure sign of trouble when leading insurance industry executives are worried about their own prices going up. Two separate CEOs of major insurance giants remarked in recent weeks about a considerable jump in cyber insurance premium prices: AIG’s chief executive said rates increased by 40% for its clients, while Chubb’s chief executive said that company was charging more, too.
- “Bangkok Air confirms passenger PII leak after ransomware attack” By Catalin Cimpanu — The Record. Bangkok Airways, the second oldest and the third biggest airline company in Thailand, has admitted last week that hackers stole passenger information during a security breach following a ransomware attack. The airline confirmed the breach in a press release last Thursday, a day after a ransomware gang known as LockBit posted a message on its dark web portal threatening the company to leak data if it didn’t pay a hefty ransom demand.
- “Britain tries to work out what a journalist is” By Annabelle Dickson — Politico EU. The U.K. wants to protect journalists from plans to regulate Big Tech — it just doesn’t seem to know how. Amid a growing chorus of concern over the impact a social media platform crackdown could have on freedom of expression, U.K. Digital Secretary Oliver Dowden vowed to place “a protective bubble around journalistic and ‘democratically important’ content” in his upcoming Online Safety Bill. But tech industry figures involved in behind-the-scenes discussions on the draft law, which is aimed at shielding internet users from harmful content, say their calls for more clarity — including specifying whose output would be protected under the Bill — are going unanswered.
- “Facebook’s Reason for Banning Researchers Doesn’t Hold Up” By Gilad Edelman — WIRED. When Facebook said Tuesday that it was suspending the accounts of a team of NYU researchers, it made it seem like the company’s hands were tied. The team had been crowdsourcing data on political ad targeting via a browser extension, something Facebook had repeatedly warned them was not allowed. “For months, we’ve attempted to work with New York University to provide three of their researchers the precise access they’ve asked for in a privacy-protected way,” wrote Mike Clark, Facebook’s product management director, in a blog post. “We took these actions to stop unauthorized scraping and protect people’s privacy in line with our privacy program under the FTC Order.”
- “Cyber experts seek clarity on NIST supply chain framework” By Dave Nyczepir — cyberscoop.Cyber experts agree a technology supply chain security framework developed by the National Institute of Standards and Technology will be a useful tool for agencies and industry. They are less sure about what it will look like. The White House gave few details in the fact sheet it released — following President Biden‘s Wednesday meeting with private sector and education leaders on improving national cybersecurity — other than the guidance will address building and assessing the security of technology like open-source software.
- “Lawyers, Bugs, and Money: When Bug Bounties Went Boom” By Dennis Fisher — Decipher. For as long as there have been computers, there have been bugs. That’s damn near 100 years and an uncountable number of bugs, some big, some small, some with wings, some that lived for decades. If they were discovered at all, most of those bugs were probably found by the developers themselves or another technical user and then fixed without much fuss. It wasn’t until much later that some bugs became security concerns and developers and researchers began thinking about them in terms of their potential effects on the confidentiality, integrity, and availability of a system. Finding and fixing bugs was gradually becoming both more difficult and more important. In 1983, Hunter & Ready was so confident in the quality of its new VRTX real-time operating system that the company offered to reward anyone who found a bug in it with a Volkswagen Beetle. “But don’t feel bad if a year from now there isn’t a bug in your driveway. There isn’t one in your operating system either,” the magazine ad said. It was a clever idea but it didn’t inspire many imitators. Not until 1995 when a startup called Netscape Communications offered cash and Netscape merchandise to people who reported security bugs in the new beta release of its Navigator 2.0 browser.
- “What are dark patterns? An online media expert explains” By Jasmine McNealy — The Conversation. Dark patterns are design elements that deliberately obscure, mislead, coerce and/or deceive website visitors into making unintended and possibly harmful choices. Dark patterns can be found in many kinds of sites and are used by several kinds of organizations. They take the form of deceptively labeled buttons, choices that are difficult to undo and graphical elements like color and shading that direct users’ attention to or away from certain options.
- “The App With the Unprintable Name That Wants to Give Power to Creators” By Taylor Lorenz — The New York Times. Six years ago, Lindsey Lee Lugrin, a budding social media creator and model, was given the chance to be featured in a Marc by Marc Jacobs ad campaign. She was paid $1,000. Ms. Lugrin was thrilled. But after seeing her face plastered on billboards and in ads across the internet, she realized she had undervalued herself. As she spoke with more influencers, who create social media posts for brands in exchange for payment or a cut of advertising fees, Ms. Lugrin became aware of other pay disparities. Male creators earned an average of $476 per post and women $348, according to an analysis last year by Klear, an influencer marketing platform.
Coming Events
- 7 September
- The California Privacy Protection Agency Board hold a public meeting.
- 8 September
- Australia’s Select Committee on Australia as a Technology and Financial Centre will hold a hearing on its inquiry.
- The California Privacy Protection Agency Board hold a public meeting.
- The U.S.-China Economic and Security Review Commission will hold a hearing on “U.S.-China Relations in 2021: Emerging Risks.”
- 9 September
- The House Science, Space, and Technology Committee will mark up its portion of the FY 2022 budget reconciliation package.
- The United Kingdom’s Digital, Culture, Media and Sport Committee will hold a meeting on the nomination of New Zealand’s Privacy Commissioner John Edwards to be the next UK Information Commissioner.
- 10 September
- The House Agriculture Committee will mark up its portion of the FY 2022 budget reconciliation package.
- 14 September
- The European Data Protection Board (EDPB) will hold a plenary meeting.
- 28 September
- The Information Security and Privacy Advisory Board (ISPAB) will hold an open meeting and “The agenda is expected to include the following items:
- —Board Discussion on Executive Order 14028, Improving the Nation’s Cybersecurity (May 12, 2021) deliverables and impacts to date,
- —Presentation by NIST, the Department of Homeland Security, and the General Services Administration on upcoming work specified in Executive Order 14028,
- —Presentation by the Office of Management and Budget on Executive Order 14028 directions and memoranda to U.S. Federal Agencies,
- —Board Discussion on recommendations and issues related to Executive Order 14028.
- The Information Security and Privacy Advisory Board (ISPAB) will hold an open meeting and “The agenda is expected to include the following items:
- 30 September
- The Federal Communications Commission (FCC) will hold an open meeting. No agenda has been announced as of yet.
© Michael Kans, Michael Kans Blog and michaelkans.blog, 2019-2021. Unauthorized use and/or duplication of this material without express and written permission from this site’s author and/or owner is strictly prohibited. Excerpts and links may be used, provided that full and clear credit is given to Michael Kans, Michael Kans Blog, and michaelkans.blog with appropriate and specific direction to the original content.
Photo by Denise Jans on Unsplash
Photo by Vitaly Otinov on Unsplash