
Subscribe to my newsletter, The Wavelength, if you want the content on my blog delivered to your inbox four times a week. The Wavelength will transition to a subscription product early in 2022. Posts on this site will continue in a fashion. Details to come.
Other Developments
- A United States (U.S.) court issued a permanent injunction against Apple “from prohibiting developers from (i) including in their apps and their metadata buttons, external links, or other calls to action that direct customers to purchasing mechanisms, in addition to In-App Purchasing and (ii) communicating with customers through points of contact obtained voluntarily from customers through account registration within the app.” This ruling comes from the litigation brought by Epic Games for the 30% fee Apple and Google demand of all in-app purchases on smartphones while barring suers from sideloading apps. The court found Apple violated California and not U.S. competition law. The court also ordered Epic Games to pay Apple “(1) damages in an amount equal to (i) 30% of the $12,167,719 in revenue Epic Games collected from users in the Fortnite app on iOS through Epic Direct Payment between August and October 2020, plus (ii) 30% of any such revenue Epic Games collected from November 1, 2020 through the date of judgment, and interest according to law.” Epic has announced plans to appeal, and the company’s CEO said this on Twitter:
- The White House announced that President Joe Biden nominated law school professor and privacy champion Alvaro Bedoya to be a Commissioner of the Federal Trade Commission (FTC). The White House provided this biography:
- Alvaro Bedoya is the founding director of the Center on Privacy & Technology at Georgetown Law, where he is a visiting professor of law. His research and advocacy focus on the idea that privacy is for everyone. His exposés on the harms of face recognition technology have helped usher the passage of face recognition restrictions across the country, led the National Institute of Standards & Technology to conduct the first comprehensive bias audit of face recognition algorithms, and paved the way for a federal law requiring bias testing in airport face recognition systems, section 1919 of the FAA Reauthorization Act of 2018. He also co-led a coalition that successfully pressed an Internet giant to drop ads for online payday loans, which were often served in response to searches like “I need money to pay rent” or “I need money for groceries.” Previously, Bedoya served as the first chief counsel to the U.S. Senate Judiciary Subcommittee on Privacy, Technology and the Law upon the subcommittee’s creation in 2011. As a Senate staffer, Bedoya drafted bipartisan legislation to protect victims of sexual assault, conducted oversight hearings of technology companies, and helped negotiate and draft bipartisan legislation to rein in the National Security Agency.
- A naturalized citizen born in Peru, Bedoya co-founded the Esperanza Education Fund, a status-blind college scholarship that has awarded over $1 million to immigrant and first-generation students in Maryland, Virginia, and the District of Columbia. He currently serves on the Board of Directors of CASA and CASA in Action. A graduate of Harvard College and Yale Law School, Bedoya lives in Rockville, Maryland with his wife, Dr. Sima Zadeh Bedoya, a pediatric psychologist at the National Institutes of Health’s National Cancer Institute. They have two toddlers.
- The High Court of Australia has issued a decision that denied an appeal of media organizations from an appellate court’s ruling that these companies were liable for the defamatory comments people made about the subject of a news story posted to the outlets’ Facebook page. In a summary, the court explained:
- The appellants are media companies which publish newspapers that circulate in New South Wales or operate television stations, or both. Each appellant maintained a public Facebook page on which they posted content relating to news stories and provided hyperlinks to those stories on their website. After posting content relating to particular news stories referring to Mr Voller, including posts concerning his incarceration in a juvenile justice detention centre in the Northern Territory, a number of third-party Facebook users responded with comments that were alleged to be defamatory of Mr Voller. Mr Voller brought proceedings against the appellants alleging that they were liable for defamation as the publishers of those comments.
- The High Court by majority dismissed the appeals and found that the appellants were the publishers of the third-party Facebook user comments. A majority of the Court held that the liability of a person as a publisher depends upon whether that person, by facilitating and encouraging the relevant communication, “participated” in the communication of the defamatory matter to a third person. The majority rejected the appellants’ argument that for a person to be a publisher they must know of the relevant defamatory matter and intend to convey it. Each appellant, by the creation of a public Facebook page and the posting of content on that page, facilitated, encouraged and thereby assisted the publication of comments from third-party Facebook users. The appellants were therefore publishers of the third-party comments.
- The United Kingdom’s (UK) Department for Digital, Culture, Media & Sport (DCMS) launched a consultation “on reforms to create an ambitious, pro-growth and innovation-friendly data protection regime that underpins the trustworthy use of data” per the agency’s press release. DCMS stated:
- Unlocking the power of data is one of the government’s 10 Tech Priorities. As set out in the National Data Strategy, data is a strategic asset and its responsible use should be seen as a huge opportunity to embrace. This consultation is the first step in delivering on Mission 2 of the National Data Strategy to secure a pro-growth and trusted data regime.
- Outside of the EU, the UK can reshape its approach to regulation and seize opportunities with its new regulatory freedoms, helping to drive growth, innovation and competition across the country. The UK needs agile and adaptable data protection laws that enhance its global reputation as a hub for responsible data-driven business that respects high standards of data protection.
- This consultation presents proposals that build on the key elements of the current UK General Data Protection Regulation (UK GDPR), such as its data processing principles, its data rights for citizens, and its mechanisms for supervision and enforcement. The proposals aim to deliver an even better data protection regime that will: Support vibrant competition and innovation to drive economic growth
- Maintain high data protection standards without creating unnecessary barriers to responsible data use
- keep pace with the rapid innovation of data-intensive technologies
- help innovative businesses of all sizes to use data responsibly without undue uncertainty or risk, both in the UK and internationally
- ensure the Information Commissioner’s Office (ICO) is equipped to regulate effectively in an increasingly data-driven world
- This consultation is the first step in the process of reforming the UK’s regime for the protection of personal data. Consultation responses will provide us with evidence to help shape any future reforms. We are keen to hear from as broad a set of respondents as possible.
- The United Kingdom’s (UK) Department for Digital, Culture, Media & Sport (DCMS) also issued a policy paper titled “National Data Strategy monitoring and evaluation framework” DCMS explained:
- The National Data Strategy was originally published as a consultation in September 2020 and set out our proposals for how best to unlock the value of data in the UK. In May 2021, we then published the government’s response to the consultation which confirmed that government’s focus would now turn to implementation of the strategy.
- To do this, we have created a monitoring and evaluation framework for the National Data Strategy. This will track delivery of government’s interventions, assess their effectiveness, and enable us to plan for further interventions in the future.
- The framework has three guiding principles for how monitoring and evaluation of the National Data Strategy will operate:
- Dynamic and forward looking: a framework with a strategic focus, tied to delivering real-world impacts and keeping the National Data Strategy relevant in the ever-evolving context of data and digital.
- Outcome-oriented: a framework which focuses on the delivery of the key strategic priorities for the National Data Strategy, and achieving results.
- Proportionate: a framework focused on taking the most appropriate approach which adds genuine value to the work under the National Data Strategy, and which doesn’t exist to simply ‘tick a box’.
- The framework is comprised of three core elements, drawing on the original National Data Strategy framework:
- Monitoring the delivery of the five missions and the actions committed to in the September publication, to enable us to measure progress.
- Tracking the status of the data opportunities and pillars of effective data use, to enable us to understand the UK’s data-ecosystem.
- Evaluating the effectiveness of the five missions in delivering their objectives, to enable us to assess the success of our prioritised areas of action.
- The Federal Trade Commission (FTC) stated that it “approved final revisions that would bring several rules that implement parts of the Fair Credit Reporting Act (FCRA) in line with the Dodd-Frank Wall Street Reform and Consumer Protection Act (Dodd-Frank Act):
- Address Discrepancy Rule, which outlines the obligations of users of consumer reports when they receive a notice of address discrepancy from a nationwide consumer reporting agency (CRA);
- Affiliate Marketing Rule, which gives consumers the right to restrict a person from using certain information obtained from an affiliate to make solicitations to the consumer;
- Furnisher Rule, which requires entities that furnish information to CRAs to establish and implement reasonable written policies and procedures regarding the accuracy and integrity of the information relating to consumers provided to a CRA;
- Pre-screen Opt-Out Notice Rule, which outlines requirements for those who use consumer report information to make unsolicited credit or insurance offers to consumers; and
- Risk-Based Pricing Rule, which requires those who use information from a consumer report to offer less favorable terms to consumers to provide them with a notice about the use of such data.
- In addition to the technical changes to the five rules, the Pre-Screen Opt-Out Rule also added the web address where consumers can opt-out of credit offers to the model notices that motor vehicle dealers can use. The Risk-Based Pricing Rule also was updated to include examples that reflect its narrower scope to just motor vehicle dealers. The FTC has created a web page with tips for consumers with poor credit.
- The Office of the Australian Information Commissioner and “state and territory privacy regulators have produced the following guidelines to support health authorities to implement a nationally consistent approach to requirements for businesses and venues to collect contact information.” The OAIC explained:
- The non-binding guidelines are intended to be used by state and territory governments when drafting and updating requirements and designing methods to require collection of contact information from individuals by a business or venue. This includes collection via digital check-in services such as apps and QR codes.
- As domestic border restrictions change, harmonisation of requirements to collect personal information ensure personal information is handled consistently. This supports businesses and venues to develop solutions to meet the requirements, and individuals to confidently provide accurate personal information for contact tracing purposes. Protecting personal information is central to maintaining public trust and promoting compliance with health orders and contact tracing processes.
- Currently state and territory orders have some common requirements, but others differ. These guidelines suggest ways to harmonise these requirements.
- These guidelines apply to the collection of personal information for contact tracing purposes by all entities, including businesses and venues, digital check-in providers and state and territory government agencies (including through state and territory apps and QR codes).
- Data minimisation
- State and territory orders that require contact details to be collected for contact tracing purposes should be limited to the minimum information necessary for that purpose.
- This means that a business or venue should only be required to collect:
- a first name or pseudonym (where practicable)
- a contact phone number or email address or, where this information is not available, other means of contacting the individual, and
- the time and date of attendance at the business or venue
- unless the collection of more personal information is required to meet the public health objectives.
- Businesses should not collect any other information as part of the collection of personal information for contact tracing purposes.
- Security
- Contact information should be required to be protected from disclosure to other customers and securely stored by the business or venue, or their chosen provider (where the business or venue is using a third-party digital check-in service).
- Reasonable steps should be required to be taken to protect the information from misuse, interference and loss, and from unauthorised access, modification or disclosure. This includes using reasonable physical and/or ICT controls to limit access to the information, including encryption at rest and in transit, wherever feasible. Further guidance on ‘reasonable steps’ can be found in OAIC’s APP 11 Guidelines and Guide to securing personal information.
- In line with community expectations, the information should be stored in Australia.
- Contact information collected by a business or venue should be required to be securely transmitted to the relevant health department for contact tracing purposes. Where a third-party digital check-in service is used, it is preferable for the contact information to be securely transmitted directly from the provider to the health department, rather than via the business or venue.
- Purpose limitation
- Information that is collected by a business or venue solely for contact tracing purposes should be required to:
- only be used and disclosed to health authorities for contact tracing purposes
- not be used or disclosed for any other purpose, such as direct marketing or for commercial distribution
- unless secondary uses and disclosures are required by law (for example, in compliance with a court order).
- Where a business or venue collects information for more than one lawful purpose that must be clearly explained prior to collection. Each state and territory public health order must specify the extent to which other uses or disclosures may occur, for example, for law enforcement purposes. Health orders that expressly prohibit access to contact tracing data for law enforcement purposes protect personal information and increase community trust and confidence in using QR Codes.
- Retention/deletion
- Information in hard copy or electronic form that is required to be collected by a business or venue for contact tracing purposes should be required to be securely destroyed after a maximum of 28 days (including backup contact tracing data). This requirement should apply to all entities, including those collecting personal information on behalf of businesses, such as digital check-in providers and state and territory based apps and QR codes. Further guidance on the reasonable steps that can be taken to destroy personal information can be found in OAIC’s APP 11 Guidelines and Guide to securing personal information.
- Regulation by the Privacy Act or a state or territory privacy law
- Personal information collected by a business or venue for contact tracing purposes should be protected by an enforceable privacy law to ensure that individuals have redress if their information is mishandled:
- A business or venue operating a digital check-in service should choose a third-party provider that is covered by Commonwealth, state or territory privacy law or one that has opted in to coverage of the Privacy Act 1988.
- Digital check-in providers which are not already covered by Commonwealth, state or territory privacy law should opt in to coverage under the Privacy Act (s6EA).
- If a business or venue has developed its own digital check-in service, and it is not already covered by the Privacy Act, it should opt in to coverage (s6EA).
- States which are implementing government-developed digital check-in services, and which do not have enforceable privacy laws, may choose to opt into coverage of the Privacy Act (s6F) by requesting to be prescribed by the Regulations. This would extend rights and protections to residents of other states and territories where their information is being shared with a state which does not have standalone privacy laws in place.
- If a business or venue opts in to coverage of the Privacy Act, that business or venue may revoke such a choice under subsection 33(3) of the Acts Interpretation Act 1901. Similarly, if a State authority has been prescribed under section 6F, that State authority may be un-prescribed under subsection 33(3) of the Acts Interpretation Act. Information on how to opt in to the coverage of the Privacy Act can be found on the OAIC website.
- Personal information collected by a business or venue for contact tracing purposes should be protected by an enforceable privacy law to ensure that individuals have redress if their information is mishandled:
- The Dutch, German, and French governments have proposed two more changes to the “Digital Markets Act” (DMA) the European Commission (EC) has proposed as part of its shakeup and reform of how the European Union (EU) regulates the digital and online worlds. The agencies working together have dubbed themselves the “Friends of an Effective DMA” and are proposing: “the introduction of a tailor-made remediation provision and the reinforcement of the role of national authorities in the enforcement of DMA.” Here is more detail on both:
- In our paper we have called for more future-proofness and tailor-made remediation to cope with the reality of digital markets. Digital markets and gatekeepers’ strategies therein change rapidly. This requires dynamic and agile regulation that can adapt to these circumstances, specifically because preventing damage is much easier in these markets than attempting to reverse it. Furthermore, while we welcome the speed that the self-executing obligations in articles 5 and 6 of the DMA provide, for some gatekeepers’ practises more may be needed. However, due to the heterogeneity of gatekeepers and the markets in which they operate, adding further intervention possibilities to the lists in these articles might not be proportional and could risk harming innovation. We want a regulation that is both future-proof and allowing, if necessary, for a dedicated remediation tailored to the specific business model of each gatekeeper. In that way, DMA regulation should neither be too weak nor too heavy-handed. To this end, we have developed an instrument with which additional obligations could be imposed on gatekeepers.
- The DMA serves the purpose of contributing to the proper functioning of the internal market by laying down harmonised rules ensuring contestable and fair markets in the digital sector. Centralizing certain powers at EU level, such as gatekeepers’ designation or regulatory dialogue with gatekeepers improves effectiveness and prevents fragmentation. However, enforcing the DMA will need substantial dedicated staff with expertise to match the resources of the gatekeepers. National competition authorities should therefore be able to properly support the Commission and contribute with their capacities in the DMA enforcement, within a referral system similar to the one currently already in use in merger control. Since the DMA complements European and national competition law, which continues to apply alongside the DMA, this better involvement of national competition authorities within the DMA enforcement would also help to keep and create synergies in enforcement. For a coherent application of both legal regimes, close coordination and cooperation between the European Commission and in particular national competition authorities is indeed essential.
- The California legislature has passed AB-701 “Warehouse distribution centers,” a bill widely seen as being aimed squarely at Amazon. Assemblywoman Lorena Gonzalez (D-San Diego) was the primary sponsor of the bill and asserted in her press release:
- The increasing shift by online e-commerce giants like Amazon to provide faster shipping rates has contributed to an alarming increase in warehouse workers’ injury rates. Today, Assembly Bill 701 by Assemblywoman Lorena Gonzalez (D-San Diego) to create the nation’s first transparency requirements and protections against abusive warehouse quota systems is heading to Governor Gavin Newsom for his consideration.
- Companies like Amazon have taken advantage of a gap in labor law, which is silent on safe production quotas and work speeds. Minutes between scanning packages where an algorithm detects a worker is “off-task” can result in automatic discipline and even termination, forcing many workers to neglect basic needs like using the bathroom or skipping safety protocols. According to recent data on warehousing injuries during the pandemic, this working environment has resulted in Amazon warehouse workers experiencing serious injuries at a rate nearly 80 percent higher than the serious injury rate for all other employers in the warehousing industry in 2020.
- The most recent bill summary the legislature issued explained that the bill:
- Requires specified employers of 100 or more nonexempt employees at a single warehouse distribution center or 1000 or more nonexempt employees at one or more warehouse distribution centers in the state to provide each employee with a written description of each quota they are subject to within a defined time period and any potential adverse action that could result from a failure to meet the quota.
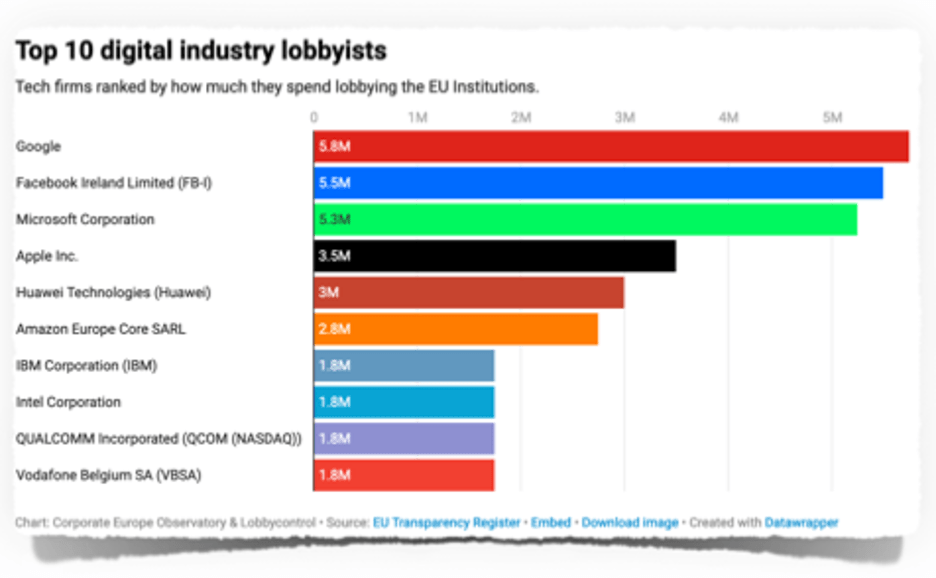
- Corporate Europe Observatory and Lobbycontrol published a report titled “The Lobby Network” that purports to “offer an overview of the tech industry’s EU lobbying firepower.” The groups asserted “[w]e found a wide yet deeply imbalanced ‘universe’:
- with 612 companies, groups and business associations lobbying the EU’s digital economy policies. Together, they spend over €97 million annually lobbying the EU institutions. This makes tech the biggest lobby sector in the EU by spending, ahead of pharma, fossil fuels, finance, and chemicals.
- in spite of the varied number of players, this universe is dominated by a handful of firms. Just ten companies are responsible for almost a third of the total tech lobby spend: Vodafone, Qualcomm, Intel, IBM, Amazon, Huawei, Apple, Microsoft, Facebook and Google spend more than €32 million making their voices heard in the EU.
- out of all the companies lobbying the EU on digital policy, 20 per cent are US based, though this number is likely even higher. Less than 1 per cent have head offices in China or Hong Kong. This implies Chinese firms have so far not invested in EU lobbying quite as heavily as their US counterparts.
- digital industry companies are not just lobbying individually. They are also collectively organised into business and trade associations which are themselves important lobby actors. The business associations lobbying on behalf of Big Tech alone have a lobbying budget that far surpasses that of the bottom 75 per cent of the companies in the digital industry.
- A number of civil rights, human rights, and advocacy organizations wrote President Joe Biden, urging him “to fill the vacancies on the Privacy and Civil Liberties Oversight Board (PCLOB) as expeditiously as possible and with nominees that will vigorously protect privacy and civil liberties while upholding government transparency.” They argued:
- It is critical that the PCLOB operate with a full bipartisan slate of qualified individuals with expertise in protecting privacy and civil liberties and experience in the field. We have seen what can happen when Board members fail to vigorously pursue the Board’s oversight mission. Years of work can be reduced to reports that provide little if any useful information or, worse, remain hidden from public view. The PCLOB has played a significant role in informing the public debates over the past several years regarding the operation of U.S. surveillance programs. It must be restored to its full operating capacity through the appointment of Board members dedicated to vigorous pursuit of its mission. We urge you to appoint members to the remaining open seats on the Board and restore quorum to the Board as soon as possible in order for the PCLOB to finally be able to resume its vital work.
Further Reading
- “El Salvador’s Adoption of Bitcoin Is Off to a Rocky Start” By Ephrat Livni and Oscar Lopez — The New York Times. El Salvador faced a rocky transition in its adoption of Bitcoin as legal tender on Tuesday. The government’s app for facilitating transactions — its “digital wallet” — went offline temporarily, protesters took to the streets of the capital to denounce the move, and the price of Bitcoin dropped sharply, demonstrating the volatility of the cryptocurrency market. The country is the first to use Bitcoin as an official currency, encouraging businesses and citizens to use it in everyday transactions, and the authorities struggled to smooth out glitches in the new system.
- “Apple’s Child Sex-Abuse Scanning Tool Is Too Clever for Its Own Good” By Tae Kim — Bloomberg. Apple Inc.’s plan to scan iPhones for child-abuse images is past the point of repair. A complete overhaul is in order. The company said Friday that it will delay implementation of the software following a backlash from privacy groups, security experts and many customers. Apple will spend a few months taking in additional feedback to make improvements “before releasing these critically important” features, the tech giant said.
- “ProtonMail Under Fire For Sharing ClActivist Data With French Authorities” By Karl Bode — Vice. Encrypted email provider ProtonMail is under intense scrutiny for sharing the IP address and device details of a French climate activist with French authorities, and for marketing and transparency reports critics say provided users with a false sense of anonymity and security. A French police report, first spotted by Techcrunch, indicates ProtonMail provided law enforcement the IP address and device details of a French activist protesting gentrification and climate inaction in Paris. The group drew significant attention for occupying Le Petit Cambodge—a restaurant targeted in the November 2015 terrorist attacks on the French city.
- “Pro-China Online Network Used Fake Accounts to Urge Asian-Americans to Attend Protests, Researchers Say” By Dustin Volz — The Wall Street Journal. A network of fake social-media accounts linked to the Chinese government has attempted to draw Americans out to real-world protests against anti-Asian-American racism and popular but unsubstantiated allegations that China engineered the virus that caused the Covid-19 pandemic, according to U.S. security firms. The attempts to physically mobilize Americans have so far failed, researchers said. But they represent a troubling effort reminiscent of Russia’s attempts to sow discord during the 2016 presidential election, they said. The activity represents the first known example of suspected China-linked actors targeting Americans with the apparent goal of encouraging them to attend real-world demonstrations.
- “How China’s quasi-carbon market for electric vehicles works” By Zeyi Yang — Protocol. The end of August marked the end of an annual trading window in China: For the past two months, carmakers have been trading their “New Energy Vehicle” credits in the dark. Leading electric vehicle companies like Tesla and BYD were making hundreds of millions, thanks to a three-year-old quasi-carbon market set up to boost the EV industry’s growth. While the United States just started injecting billions of dollars into its EV industry, China is already ahead of the game, with a “dual-credit” policy that Beijing adapted in 2017 from California state law. Over three years into its existence, the “dual-credit” policy, which punishes the production of fossil fuel cars and rewards the production of EVs, has become one of the most successful policies globally in incentivizing EV production. Some Chinese companies are even selling EVs below cost, as long as the revenue from selling carbon credits can make up for the shortfall.
- “China blurs borders with Macau to advance chipmaking and AI plans” By Simon Sharwood — The Register. China has revealed plans to create a special economic zone that focuses on development and manufacturing of semiconductors – and will create some fabulous geopolitical interest along the way. The new “Guangdong-Macau in-depth cooperation zone” will be located on Hengqin island, part of which is currently leased to the former Portuguese colony of Macau.
- “GAO recommends HHS reconsider $330M IT contract award to Accenture” By John Hewitt Jones — cyberscoop. The Government Accountability Office has recommended that the Department for Health and Human Services reevaluate a $330M IT contract won by Accenture Federal Services (AFS), but dismissed a competitor’s claim that the awardees’ experience was improperly evaluated. AFS was awarded the task order in April this year following a protracted solicitation process that has so far included three bid protests, the most recent of which was filed by Deloitte.
- “You’re Watching More TikTok Than YouTube, Which Is Why Every App Is Trying to Be TikTok” By Brianna Provenzano — Gizmodo. TikTok users are officially gobbling up more content than their counterparts on YouTube, with the ByteDance-owned short video platform officially outpacing the streaming giant in terms of content watched each month for the second year in a row. A recent report from the app analytics firm App Annie found that as of June 2021, TikTok users were watching more than 24 hours of content per month, compared with 22 hours and 40 minutes watched on Google-owned YouTube. The new data solidifies a trend that first emerged in August of 2020, when TikTok overtook YouTube in the U.S. for the first time. In other parts of the world, the gulf between the two streaming platforms has grown even wider: According to the same report, TikTok officially overtook YouTube in the U.K. in May of last year, with users there now reportedly taking in nearly 26 hours of content a month, as compared to less than 16 on YouTube in the same time frame.
- “Anti-Vaxxers Are Learning How To Game TikTok’s Algorithm – And They’re Going Viral” By Sophia Smith Galer — Vice. “I just wanted to show you guys – I’m NHS staff,” says an unnamed woman, as she twitches and rolls her eyes back. “I had my COVID jab on the 17th of March, that left me with seizures and I was paralysed for two weeks. But it’s left me with tic attacks. And I just wanted to show you what happens.” This TikTok spreading COVID misinformation was seen 1.2 million times, and the user, @palestine_eye_of_tiger2, gained several thousand new followers in just a few days. It’s one of more than 50 videos that the account posted over August and September which featured clips of people appearing to have seizures and describing their symptoms as an adverse effect of the COVID vaccine.
- “How the N.Y.P.D. Is Using Post-9/11 Tools on Everyday New Yorkers” By Ali Watkins — The New York Times. It was an unusual forearm tattoo that the police said led them to Luis Reyes, a 35-year-old man who was accused of stealing packages from a Manhattan building’s mailroom in 2019. But the truth was more complicated: Mr. Reyes had first been identified by the New York Police Department’s powerful facial recognition software as it analyzed surveillance video of the crime. His guilty plea this year was not solely the result of keen-eyed detectives practicing old school police work. Instead, it was part of the sprawling legacy of one of the city’s darkest days.
- “Nvidia’s EU Filing for Arm Deal Kicks Off Tough Scrutiny” By Aoife White — Bloomberg. Nvidia Corp. sought European Union approval for its plan to take over U.K.-based chip developer Arm Ltd., kick-starting a tough antitrust probe that could further thwart plans to close the deal by early next year. The European Commission set an initial Oct. 13 deadline to rule on the transaction, according to a website that showed the companies filed with regulators on Wednesday.
Coming Events
- 15 September
- The Federal Trade Commission (FTC) will hold an open meeting with the following tentative agenda:
- Proposed Policy Statement on Privacy Breaches by Health Apps and Connected Devices: The Commission will vote on whether to issue a policy statement on the importance of protecting the public from privacy breaches by health apps and other connected devices.
- Non-HSR Reported Acquisitions by Select Technology Platforms, 2010-2019: An FTC Study: Staff will present some findings from the Commission’s inquiry into large technology platforms’ unreported acquisitions, including an analysis of the structure of deals that customarily fly under enforcers’ radar. The public release of the report is subject to commission vote.
- Proposed Revisions to FTC Procedural Rules Concerning Petitions for Rulemaking: The Commission will vote on putting in place a process to receive public input on rulemaking petitions by external stakeholders.
- Proposed Withdrawal of 2020 Vertical Merger Guidelines: The Commission will vote on whether to rescind the Vertical Merger Guidelines adopted in June 2020 and the Commentary on Vertical Merger Enforcement issued in December 2020.
- The National Institute of Standards and Technology (NIST) will hold a virtual public workshop “on challenges and practical approaches to initiating cybersecurity labeling efforts for Internet of Things (IoT) devices and consumer software.” NIST added:
- The workshop will help NIST to carry out an Executive Order (EO) on Improving the Nation’s Cybersecurity. The agenda for the workshop will include facilitated panel discussions and presentations based on consumer software labeling position papers submitted to NIST and on preliminary feedback on potential IoT baseline security criteria that was shared by NIST in August.
- According to the EO, by February 6, 2022, in coordination with the Federal Trade Commission (FTC) and other agencies, NIST is required to:
- identify IoT cybersecurity criteria for a consumer labeling program and
- identify secure software development practices or criteria for a consumer software labeling program.
- The Federal Trade Commission (FTC) will hold an open meeting with the following tentative agenda:
- 23 September
- The United Kingdom’s Joint Select Committee will hold a hearing on the government’s draft “Online Safety Bill.”
- 28 September
- The Information Security and Privacy Advisory Board (ISPAB) will hold an open meeting and “The agenda is expected to include the following items:
- —Board Discussion on Executive Order 14028, Improving the Nation’s Cybersecurity (May 12, 2021) deliverables and impacts to date,
- —Presentation by NIST, the Department of Homeland Security, and the General Services Administration on upcoming work specified in Executive Order 14028,
- —Presentation by the Office of Management and Budget on Executive Order 14028 directions and memoranda to U.S. Federal Agencies,
- —Board Discussion on recommendations and issues related to Executive Order 14028.
- The Information Security and Privacy Advisory Board (ISPAB) will hold an open meeting and “The agenda is expected to include the following items:
- 30 September
- The Federal Communications Commission (FCC) will hold an open meeting with this tentative agenda:
- Promoting More Resilient Networks. The Commission will consider a Notice of Proposed Rulemaking to examine the Wireless Network Resiliency Cooperative Framework, the FCC’s network outage reporting rules, and strategies to address the effect of power outages on communications networks. (PS Docket Nos. 21-346, 15-80; ET Docket No. 04-35)
- Reassessing 4.9 GHz Band for Public Safety. The Commission will consider an Order on Reconsideration that would vacate the 2020 Sixth Report and Order, which adopted a state-by-state leasing framework for the 4.9 GHz (4940-4900 MHz) band. The Commission also will consider an Eighth Further Notice of Proposed Rulemaking that would seek comment on a nationwide framework for the 4.9 GHz band, ways to foster greater public safety use, and ways to facilitate compatible non-public safety access to the band. (WP Docket No. 07-100)
- Authorizing 6 GHz Band Automated Frequency Coordination Systems. The Commission will consider a Public Notice beginning the process for authorizing Automated Frequency Coordination Systems to govern the operation of standard-power devices in the 6 GHz band (5.925-7.125 GHz). (ET Docket No. 21-352)
- Spectrum Requirements for the Internet of Things. The Commission will consider a Notice of Inquiry seeking comment on current and future spectrum needs to enable better connectivity relating to the Internet of Things (IoT). (ET Docket No. 21-353)
- Shielding 911 Call Centers from Robocalls. The Commission will consider a Further Notice of Proposed Rulemaking to update the Commission’s rules regarding the implementation of the Public Safety Answering Point (PSAP) Do-Not-Call registry in order to protect PSAPs from unwanted robocalls. (CG Docket No. 12-129; PS Docket No. 21-343)
- Stopping Illegal Robocalls From Entering American Phone Networks. The Commission will consider a Further Notice of Proposed Rulemaking that proposes to impose obligations on gateway providers to help stop illegal robocalls originating abroad from reaching U.S. consumers and businesses. (CG Docket No. 17-59; WC Docket No. 17-97)
- Supporting Broadband for Tribal Libraries Through E-Rate. The Commission will consider a Notice of Proposed Rulemaking that proposes to update sections 54.500 and 54.501(b)(1) of the Commission’s rules to amend the definition of library and to clarify Tribal libraries are eligible for support through the E-Rate Program. (CC Docket No. 02-6)
- Strengthening Security Review of Companies with Foreign Ownership. The Commission will consider a Second Report and Order that would adopt Standard Questions – a baseline set of national security and law enforcement questions – that certain applicants with reportable foreign ownership must provide to the Executive Branch prior to or at the same time they file their applications with the Commission, thus expediting the Executive Branch’s review for national security and law enforcement concerns. (IB Docket No. 16-155)
- The Federal Communications Commission (FCC) will hold an open meeting with this tentative agenda:
© Michael Kans, Michael Kans Blog and michaelkans.blog, 2019-2022. Unauthorized use and/or duplication of this material without express and written permission from this site’s author and/or owner is strictly prohibited. Excerpts and links may be used, provided that full and clear credit is given to Michael Kans, Michael Kans Blog, and michaelkans.blog with appropriate and specific direction to the original content.
Photo by Hannah Troupe on Unsplash
Photo by Aidan Roof from Pexels